Authentication is an essential security measure to ensure the confidentiality of resources (data, applications, software, etc.).
It makes it possible to ensure that resources are only accessed by authorised persons.
How does it work?
Authentication is a mechanism involving two distinct entities: a prover and a verifier.
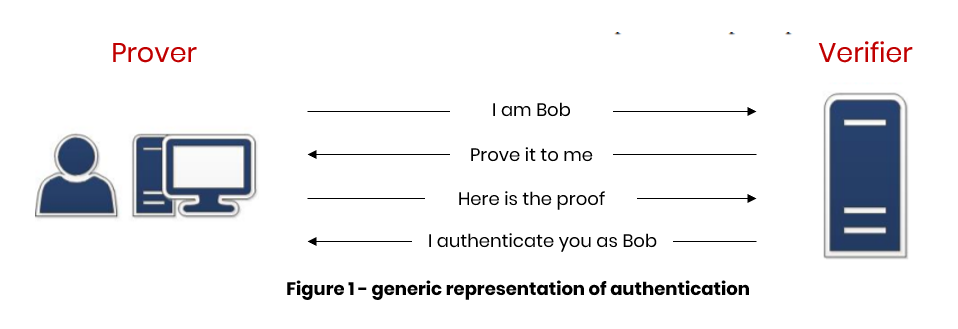 Source: Anssi - Authentication 2.0 guide
Source: Anssi - Authentication 2.0 guide
- The prover seeks to prove his identity to the verifier. For example, the prover must demonstrate his knowledge of secret data such as a password.
- The verifier must be able to ensure the validity of the identity of the prover. For example, the verifier checks the accuracy of the password provided by the prover.
Authentication is preceded by an identification phase (sometimes implicit) which consists, for the prover, in announcing his identity without proving it.
Most of the time, this is the user name.
The authentication function as such has the objective of allowing the prover to prove his identity (often announced during the identification phase).
This authentication function involves a means of authentication which can take several forms: password, encryption system, PIN (Personal Identification Number) identification, etc. which is known only to the user.
Once authenticated, the user will have access to the resources determined by the system administrator (data, software, application, customer account).
