We broke the rule: at Dastra, even the shoemakers have the best shoes.
Data privacy and security have always been at the core of our mission. We are proud to announce that Dastra is now certified ISO 27701, an international standard that attests to our compliance with best practices in data protection management.
As a platform specialized in GDPR compliance management, we found ourselves being clients of our own tool. Discover how we walk the talk!
🔒What is ISO 27701?
The standard was developed with input from global authorities, including CNIL (France’s data protection authority), AFNOR, and the European Data Protection Board. Its goal: to align data privacy requirements across multiple regulatory frameworks — not only the EU’s GDPR but also the California Consumer Privacy Act (CCPA) and Canadian privacy laws.
As a globally relevant standard, ISO 27701 represents the state of the art in privacy management. For more, see CNIL's explanation here.
Achieving ISO 27701 certification means that Dastra has achieved:
A Privacy Information Management System (PIMS) that meets strict standards for data governance and confidentiality.
Controls tailored to the processing of personal data, adapted to our role — most often as a data processor.
📍 Why pursue ISO 27701 certification?
Although Dastra already offers a solid GDPR compliance platform, our team chose to go further.
This certification was a voluntary, proactive step, demonstrating our alignment with the most demanding international standards in privacy protection — a true marker of organizational maturity and operational rigor.
In practice, certification brings:
Stronger data security and transparency
Reinforced compliance with GDPR and other global regulations
Clear governance and robust internal controls
A culture of continuous improvement in privacy and security processes
This means our clients can rely on a certified partner to help manage and protect their own data.
🧭 Assistance: Should you seek help?
The answer depends on your organization’s size, maturity, and internal knowledge of ISO requirements — particularly in audit management.
| Criteria | Service (Human Expert) |
SaaS (Software) |
Hybrid (SaaS + Service) |
|---|---|---|---|
| Strategy Transparency | 👍 Average to good, depending on the provider | ⚠️ Low: "black box" logic of the software | ✅ Total: clear, explained, personalized approach |
| Evidence Management | 👍 Average, depending on the provider | ⚠️ Limited: depends on the software's rules | ✅ Strong: manual, contextualized selection |
| Time Saving | 👍 Significant for audits, less for data collection | ✅ Very strong for data collection | ✅ Balanced: quick but supervised |
| Certification Quality | ✅ High | ⚠️Varies - depends on user setup | ✅ High (human oversight with audit alignment) |
| Cost | ❗️ Higher | ✅ Affordable | 💸 Intermediate |
| Level of required autonomy | 👍 Low: everything is guided | ❗️ High: depends on the user | 👍 Moderate: assistance available |
| Suitable for SMEs without dedicated resources? | ✅ Yes | ⚠️ Risky if the team is not trained | ✅ Yes, with support |
We have chosen the hybrid approach, in collaboration with our partner Bastion, which greatly simplified the process.
This type of assistance, while not mandatory, proves to be particularly strategic—especially in the absence of internal ISO expertise—for several key reasons, as follows:
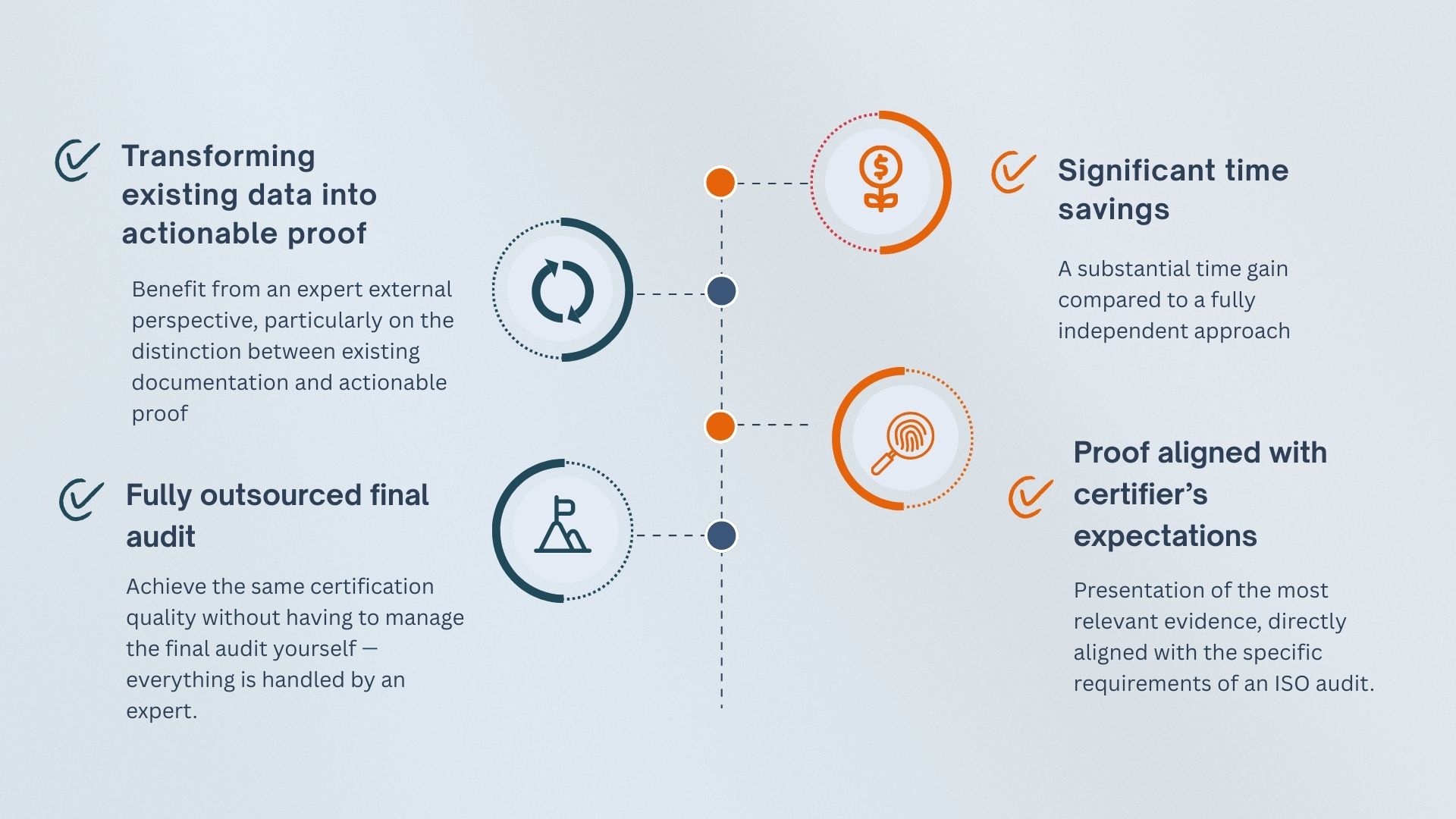
Key steps in our certification journey
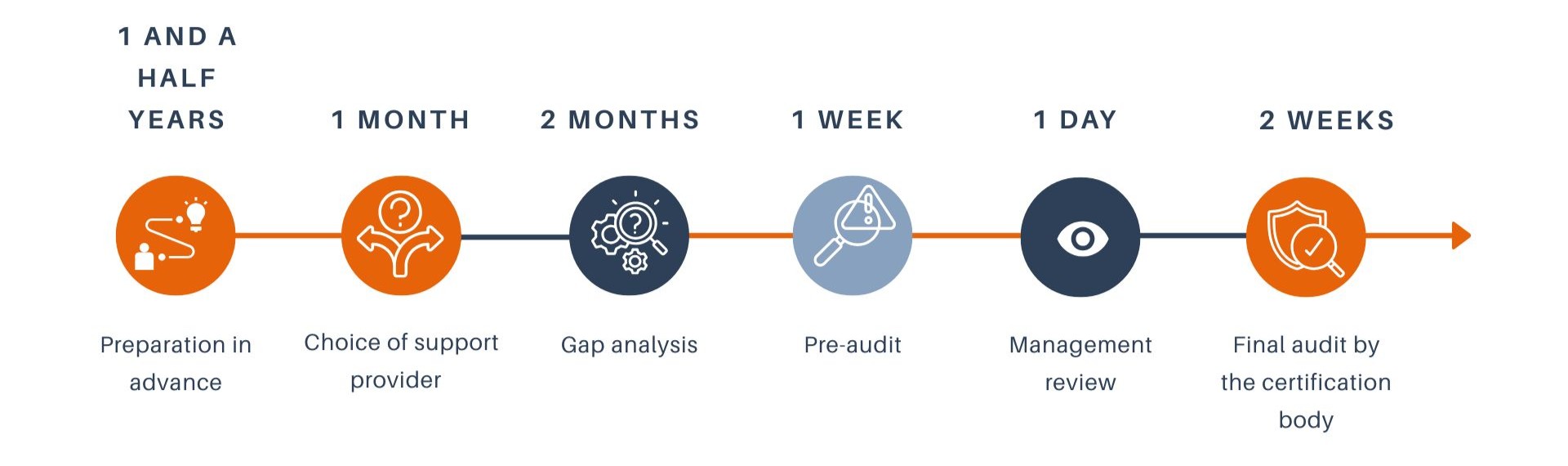
🧩 Step 1: Preparation & Governance
The project began two years ago, aiming for both ISO 27001 and ISO 27701 certifications. From the start, we set up a steering committee and appointed a lead person responsible for gathering and validating evidence.
A key success factor: cross-functional governance. Regular meetings brought together leadership, our DPO, and strategic teams — making compliance a company-wide commitment, not just a legal or tech issue.
We then assessed our existing systems and identified what was already in place (thanks to Dastra’s own tools: registers, data maps, policies), and what was missing — especially a centralized, audit-ready evidence system.
This meant:
Identifying what already existed and defining the scope
Filling the gaps and analyzing discrepancies
Structuring everything into an audit-proof system
🧩 Step 2: Building the PIMS (Privacy Information Management System)
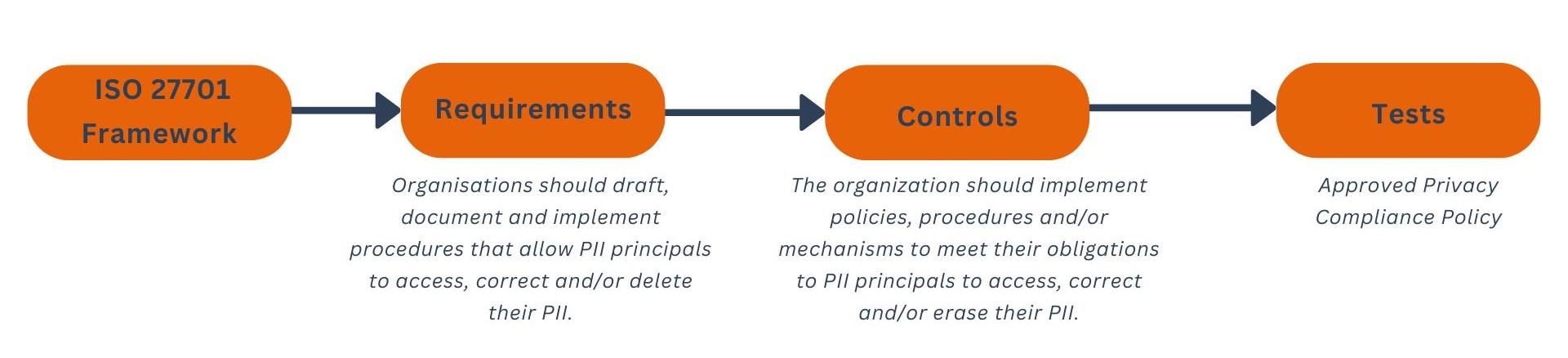 To meet ISO 27701’s requirements, we strengthened our policies and procedures related to personal data, including:
To meet ISO 27701’s requirements, we strengthened our policies and procedures related to personal data, including:
Mapping all personal data processing activities
Structuring privacy and data subject rights policies
Implementing appropriate technical and organizational measures to ensure confidentiality
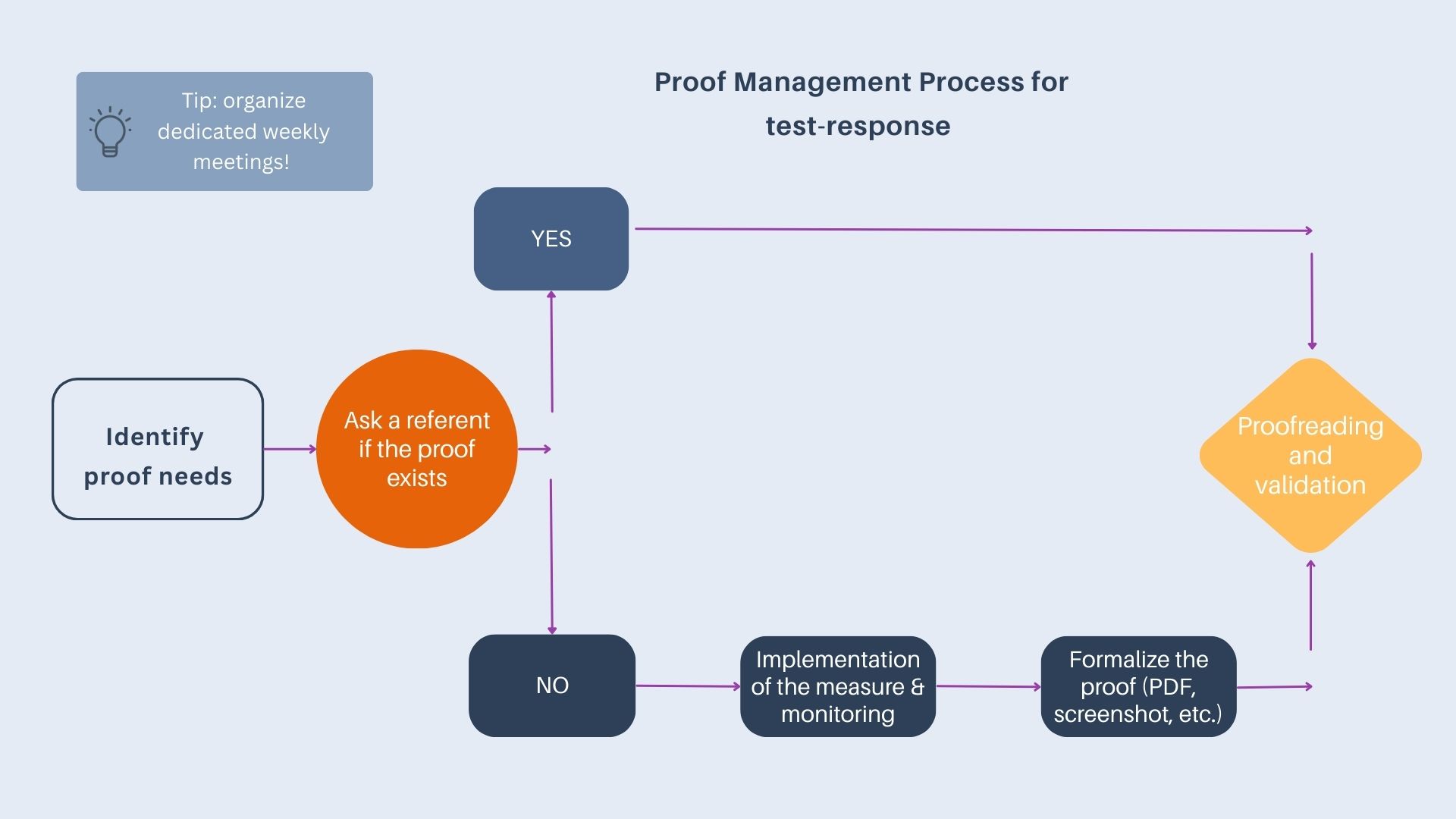
💡 A key principle of ISO audits: what’s not documented doesn’t exist. It’s not enough to implement good practices — you must prove them clearly and consistently.
Examples:
A security scan isn’t enough on its own. You must show the resulting action (e.g., patch applied, validated, deployed), with screenshots or audit logs.
At Dastra, automatic data deletion was technically in place — but the absence of a formally documented policy was noted as an area for improvement.
 Policies essential to the PIMS:
Policies essential to the PIMS:
Privacy Policy: Defines how personal data is collected, used, stored, and protected.
Data Retention Policy: Specifies the duration of data retention based on its type and purpose.
Data Deletion Policy: Describes secure methods for data and document deletion or destruction.
Data Classification Policy: Categorizes data based on sensitivity to adapt protection levels.
Encryption Policy: Defines rules for data encryption in storage and transmission.
Communication Plan in case of subcontractor changes: Frames the notification of clients and partners in case of subcontractor changes.
Terms of Service and Sales: Establishes contractual conditions between the company and its users or clients.
Up-to-date Information Security Management System (ISMS): Ensures that all policies are formalized, implemented, updated, and regularly audited.
🧩 Step 3: Internal Audit, pre-validation stage
Before the official audit, Dastra conducted an internal audit with our partner Bastion. This allowed us to:
- Verify that all ISO 27001 + 27701 requirements were effectively covered.
- Identify any non-conformities or missing proof.
- Quickly address outstanding issues.
This dry run was critical — it gave us a chance to correct weak points without pressure.
🧩 Step 4: Management Review
The process concluded with a management review involving all stakeholders—management, compliance manager, technical and product teams. This final meeting allowed us to:
- Validate all remaining proof collectively.
- Officially confirm compliance objectives had been met.
- Demonstrate strong, informed governance to the auditor.
🧩 Step 5: Certification Audit by an Accredited Body
An independent auditor then assessed our systems and confirmed our compliance with ISO 27701.
Thanks to our team's efforts and ongoing commitment to data security, Dastra successfully earned the certification.
Our team acknowledges: the journey was long but transformative. Even for a company specialized in compliance, we had to structure, prove, and formalize our practices.
Technology alone is not enough to earn a certification — it’s the alignment between tools, practices, and governance that does.
🗃️ How Dastra helped simplify proof management
As you may have guessed it, our own platform played a key role throughout the certification process.
Dastra did half the work by centralizing a significant portion of required information: registers, data maps, policies, and documentation exports — all in one place.
We essentially became our own client — and the tool became essential to meet the complex ISO requirements.
Step 1: Maintain an up-to-date Data Mapping
- List personal data used across the company
- Map systems and assets that process that data
- Link each asset to its respective sub-processors
- Document the location of those sub-processors
- Collect their security docs, SLAs, and privacy policies via the Contracts module
Step 2: Keep an up-to-date Record of processing activities
- Document the company's data processing activities
- Automatically conduct a DPIA (Data Protection Impact Assessment) for your high-risk processing activities from the Questionnaire module (PIA template)
- Automatically generate your DPAs (Data Processing Agreements)
Step 3: Export a Customized Report
- You just need to export the "Providers and datasets" report to have your subcontractors, their locations, and the datasets they have access to
Step 4: Collect Cookie Consents
- Create and publish your cookie policy
- Deploy a consent widget on your website
Step 5: Manage Data Subject Rights Requests
- Set up your Dastra Privacy Hub!
✅ What we learned from this journey
- Certification reinforces a culture of evidence, even for compliance experts.
- It forces you to formalize what’s often implicit, especially in security and privacy policies.
- It unites teams around a common goal, with clear ownership and accountability.
- It reflects a real, measurable commitment to privacy and data protection.
🎯 In summary:
ISO 27701 is more than a label.
It’s a strategic commitment that has pushed us — as a compliance platform provider — to hold ourselves to the highest standards of security and privacy.
And our clients can now count on a certified, proven partner to help them manage and secure their own data with confidence.
Would you like assistance with your ISO 27701 process?
Dastra offers a platform to help centralize your evidence, structure your policies, and document your practices — built by a team who’s been through it all.
